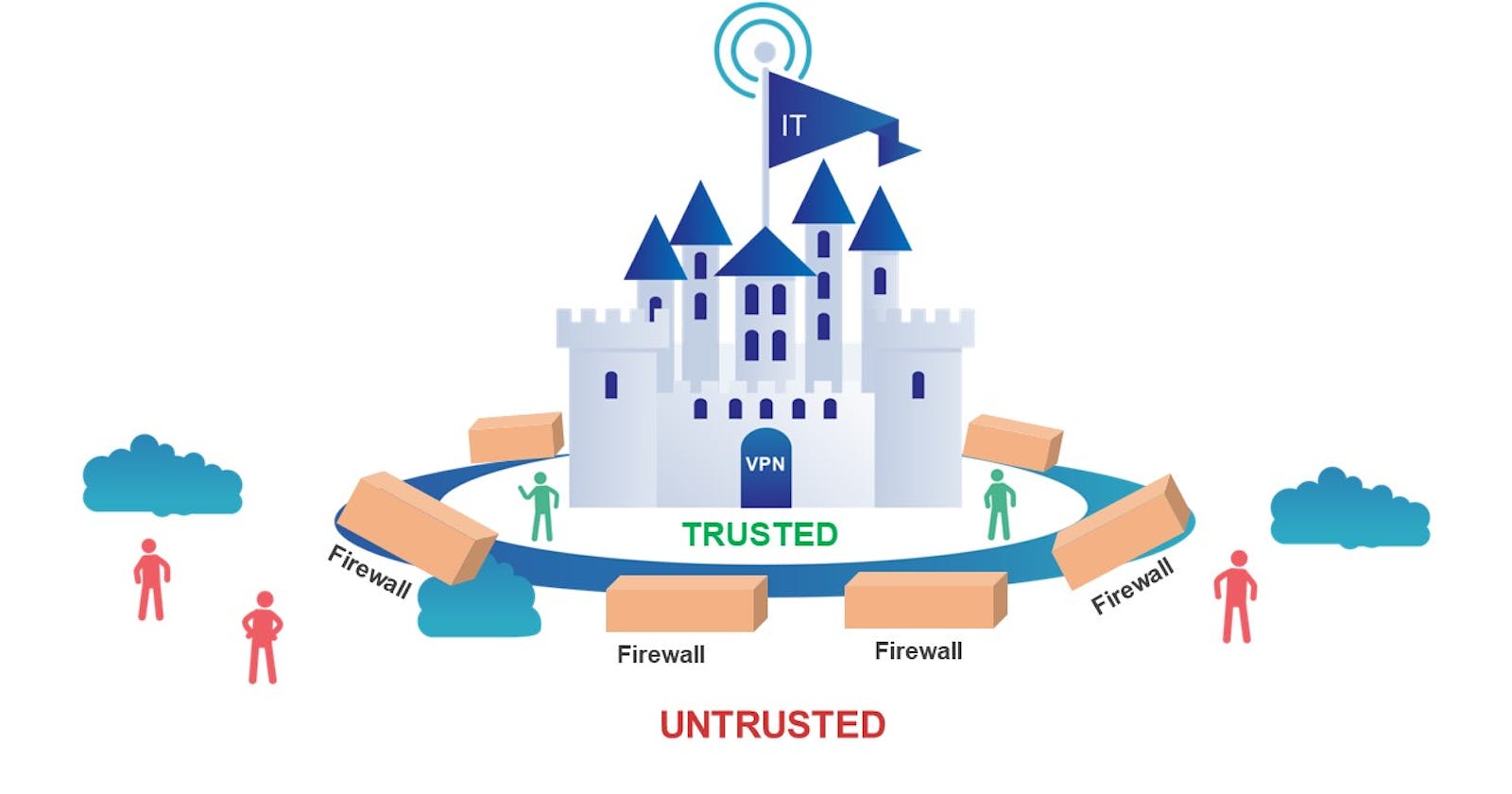
What is Zero Trust?
Zero Trust is a security model that aids in tracking threats, and platform changes based on business resources. It's an approach to secure platforms by adding additional verification steps for every user or device.
"never trust, always verify"
Zero Trust Principles
Verify Explicitly
Always authenticate & authorize for all available data points
Least Privilege Access
Limit the user's exposure by only permitting access to the resources they actually need.
Just-In-Time (JIT) limits access to resources or applications by dedicating a predetermined period of time or on an as need basis.
Just-Enough-Access (JEA) reduces the amount of administrators per machine and limits what resources users can access
Assume Breach
Verify end-to-end encryption and utilize log analytics to increase visibility on activities, threat detection, and improve defense practices.
Other Principles
Microsegmentation breaks up security parameters into smaller zones to ease the maintainability of each part of the network.
Multi-Factor Authentication (MFA) is when the user has multiple layers of evidence for determining their identity. For example, after entering a password, the user also enters a code, that's sent to a second device, such as a smartphone.
Benefits of the Zero Trust Model
Implementing Zero-Trust concepts helps reduce damage and reduce costs. Zero Trust principles are designed to minimize an organization's attack surface. These principles also help reduce the damage done because the attacker can't move laterally through the network, since it's segmented into separate zones. This means that the cost of recovery is much smaller. Zero Trust also prevents credential theft and other threats because there are multiple layers of verification and security. Overall, zero-trust protects modern IT environments, as it protects data stored inside and outside the network.
Best Practices
All devices should be updated for maintainability
Break up the network into small parts, so any breaches are detected early and contained
Hardware-based security tokens are far more secure than soft tokens like one-time passcodes
Implementing threat intelligence data can help organizations mitigate all attack tactics
Visibility into network traffic is important to ensure all users and devices are compliant
All users should have the least amount of access needed
Have a balanced amount of security measures, too much can exhaust the user
Use Cases
Remote work: zero-trust can securely extend accessibility to the network and resources from anywhere
Onboarding new employees: zero-trust can ease the process to quickly onboard multiple new internal users
Onboarding third-party users: zero-trust utilizes the principle of least privilege access, so third-party users only have access to limited, necessary resources
Replace VPNs: organizations rely on VPNs to protect data, but those are not as effective against modern attack techniques